43 aws security best practices
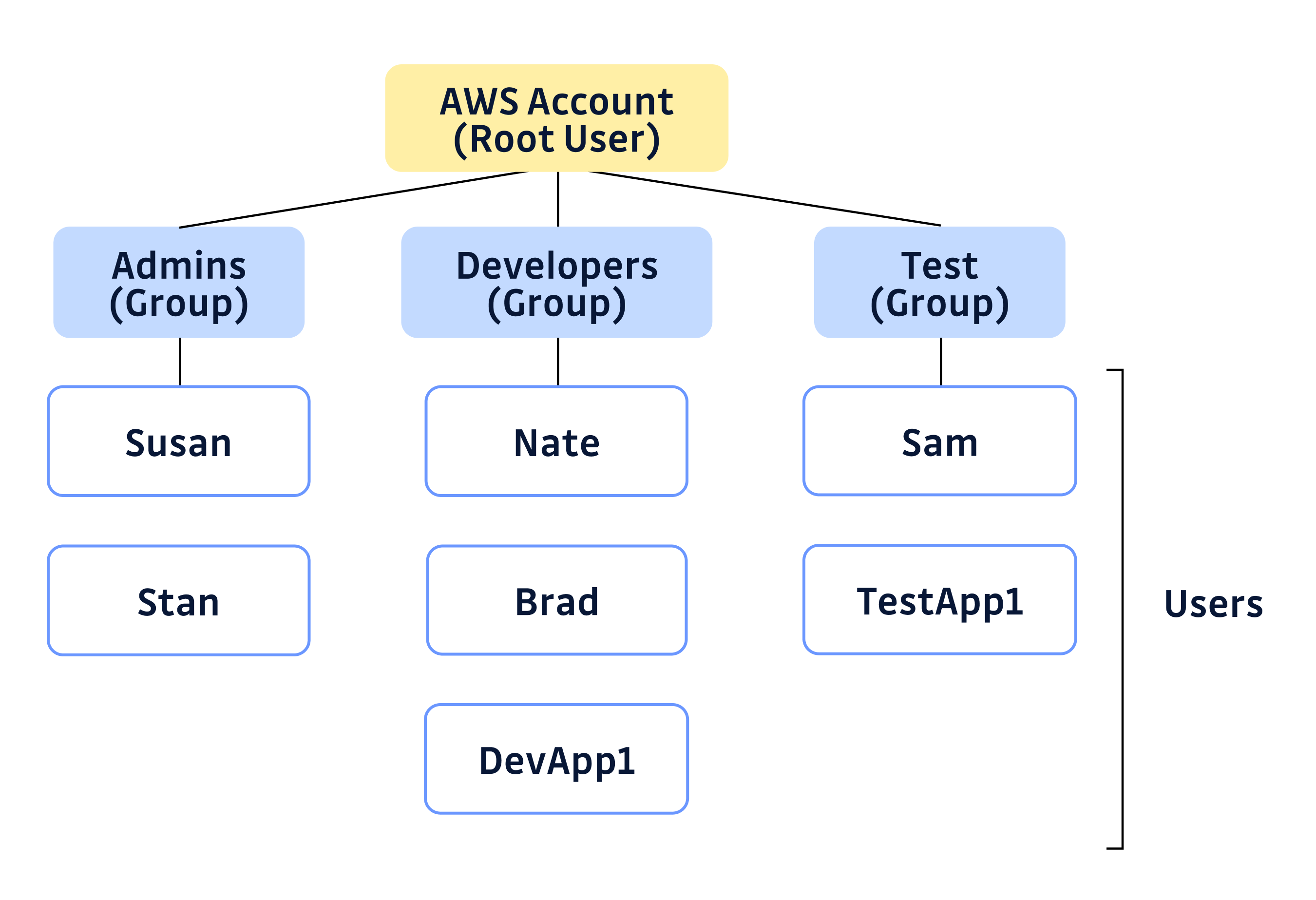
AWS — IAM Best Practices. Security Best Practices in AWS Identity… | by ... Awesome Cloud — AWS IAM Security Best Practices TL;DR: AWS Identity and Access Management (IAM) provides fine-grained access control across all of AWS. With IAM, you can specify who can access ... AWS Security Best Practices Checklist | CDW By discussing common security threats and questions with employees, you can make them feel more comfortable with AWS services. The greater an employee's knowledge of security services, the better they will be protected—and having a company culture based on cybersecurity helps to provide those benefits. 7. Maintain Regulatory Compliance
AWS VPC Security: 13 Best Practices [The 2022 Guide] - Hyperglance After all the effort, it would be silly not to utilize AWS Config, or a time-saving alternative like Hyperglance, to make sure that your best practices stay that way. The best-in-class cloud security tools include hundreds of rule-based checks (here are Hyperglance's security checks as an example). Also, look out for codeless implementations ...

Aws security best practices
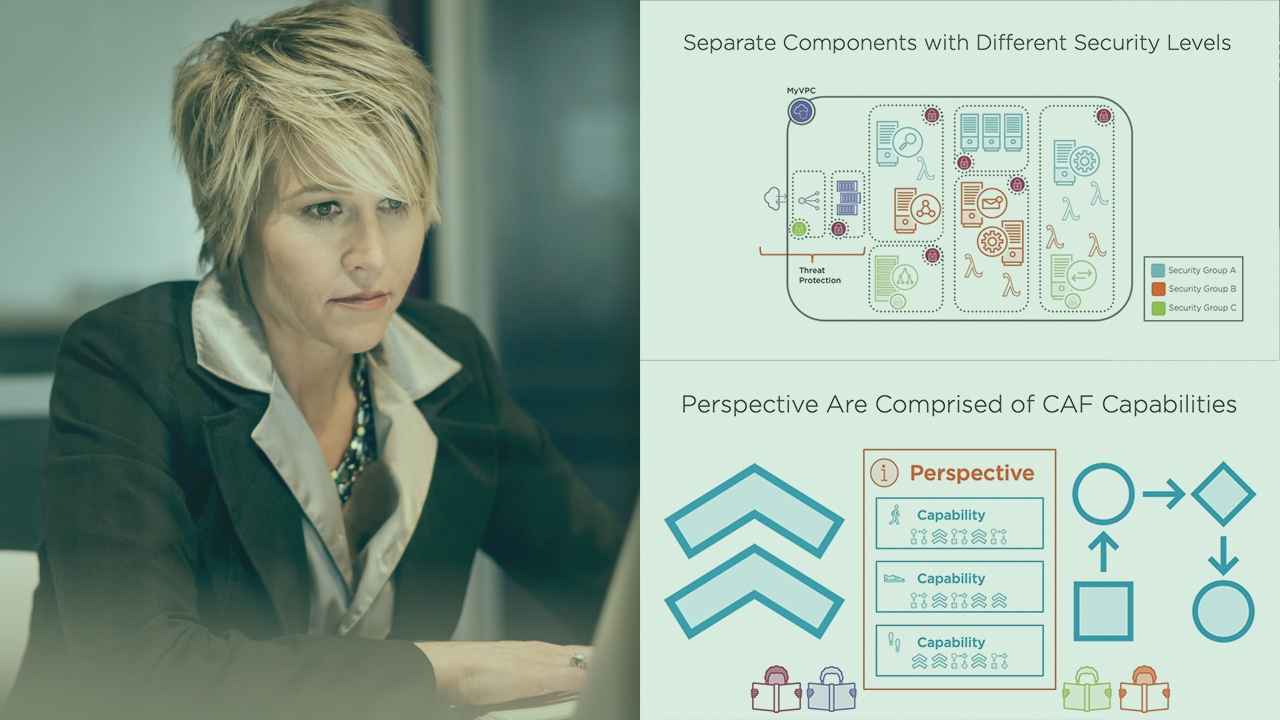
AWS Security Group: Best Practices & Instructions - CoreStack Introduction - AWS Security Best Practices Chapter 1 - AWS Security Group Best Practices Chapter 2 - S3 Security Chapter 3 - An AWS NACL Introduction Chapter 4 - API Gateway Security Chapter 5 - EBS Encryption Chapter 6 - AWS Parameter Store vs Secrets Manager Chapter 7 - Amazon Inspector Essentials Chapter 8 - IAM Best Practices AWS ECR Security Best Practices - Medium 1. Use IAM Roles for Amazon ECR. The first security best practice for ECR is to use IAM roles. IAM roles are a type of IAM identity that you can use to delegate permissions to users or services. AWS Cloud Security Best Practices - Sysdig AWS Container Security Best Practices. Like other major public clouds, AWS offers several ways to run containerized applications. The primary AWS container services include: Elastic Container Service (ECS), a managed container service that is based on an orchestrator that Amazon developed itself. Elastic Kubernetes Service (EKS), a managed ...
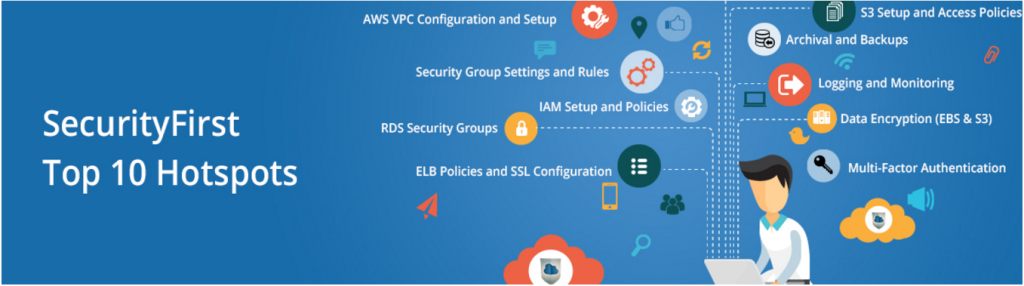
Aws security best practices. 51 AWS Security Best Practices | McAfee Blog Below are some best practices around AWS database and data storage security: Ensure that no S3 Buckets are publicly readable/writeable unless required by the business. Turn on Redshift audit logging in order to support auditing and post-incident forensic investigations for a given database. Encrypt data stored in EBS as an added layer of security. 13 AWS Security Best Practices - Check Point Software Perform Threat Hunting in AWS: A fully reactive cybersecurity policy, based on identifying and responding to in-progress attacks, places the organization at risk. By the time an attack has been identified, the attacker likely already has access to the organization's cloud-based infrastructure and is stealing data or causing other harm. 21 AWS Security Groups Best Practices | McAfee Blog As with any AWS service, it is crucial that AWS security groups are properly configured to protect against security risks and threats and best practices are followed: 1) VPC flow logging: Enable Virtual Private Cloud (VPC) flow logging. VPC flow logs provide visibility into network traffic that traverses the VPC and can be used to detect ... AWS Cloud Security Best Practices - Sysdig AWS Container Security Best Practices. Like other major public clouds, AWS offers several ways to run containerized applications. The primary AWS container services include: Elastic Container Service (ECS), a managed container service that is based on an orchestrator that Amazon developed itself. Elastic Kubernetes Service (EKS), a managed ...
AWS ECR Security Best Practices - Medium 1. Use IAM Roles for Amazon ECR. The first security best practice for ECR is to use IAM roles. IAM roles are a type of IAM identity that you can use to delegate permissions to users or services. AWS Security Group: Best Practices & Instructions - CoreStack Introduction - AWS Security Best Practices Chapter 1 - AWS Security Group Best Practices Chapter 2 - S3 Security Chapter 3 - An AWS NACL Introduction Chapter 4 - API Gateway Security Chapter 5 - EBS Encryption Chapter 6 - AWS Parameter Store vs Secrets Manager Chapter 7 - Amazon Inspector Essentials Chapter 8 - IAM Best Practices
.jpg?ixlib=gatsbyFP&auto=compress%2Cformat&fit=max&q=50)
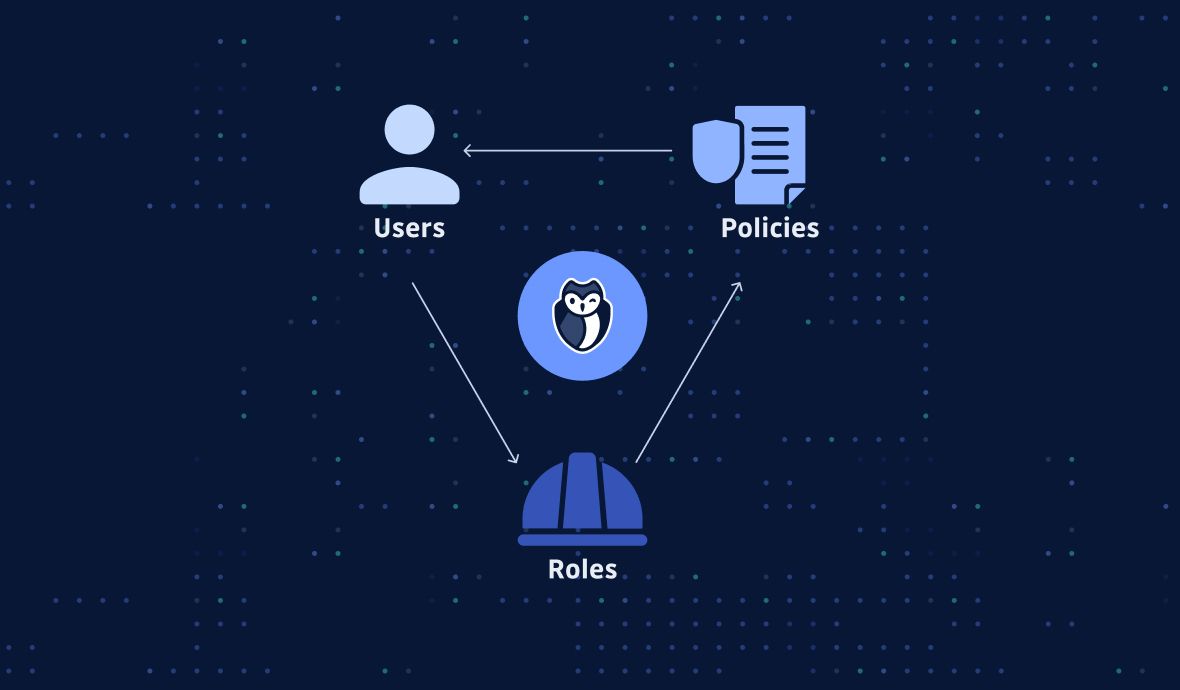


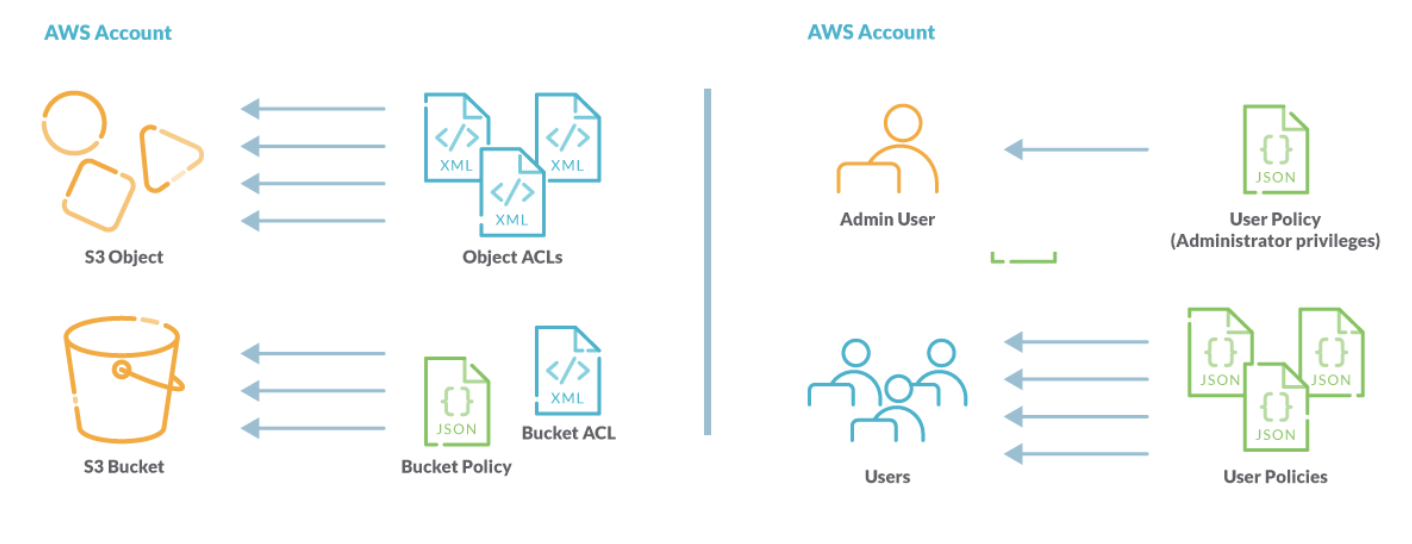

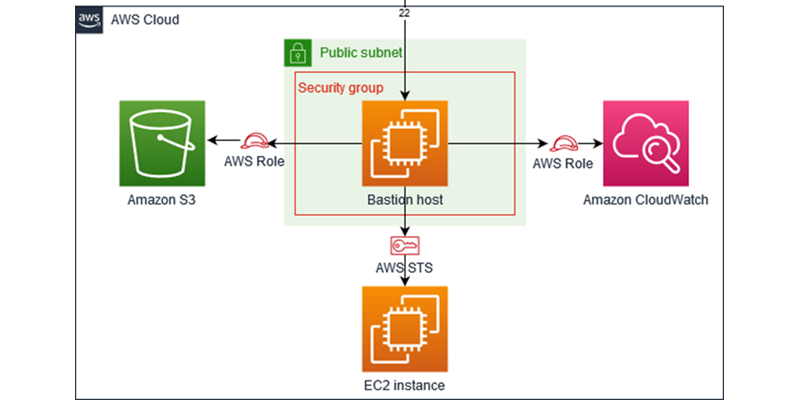









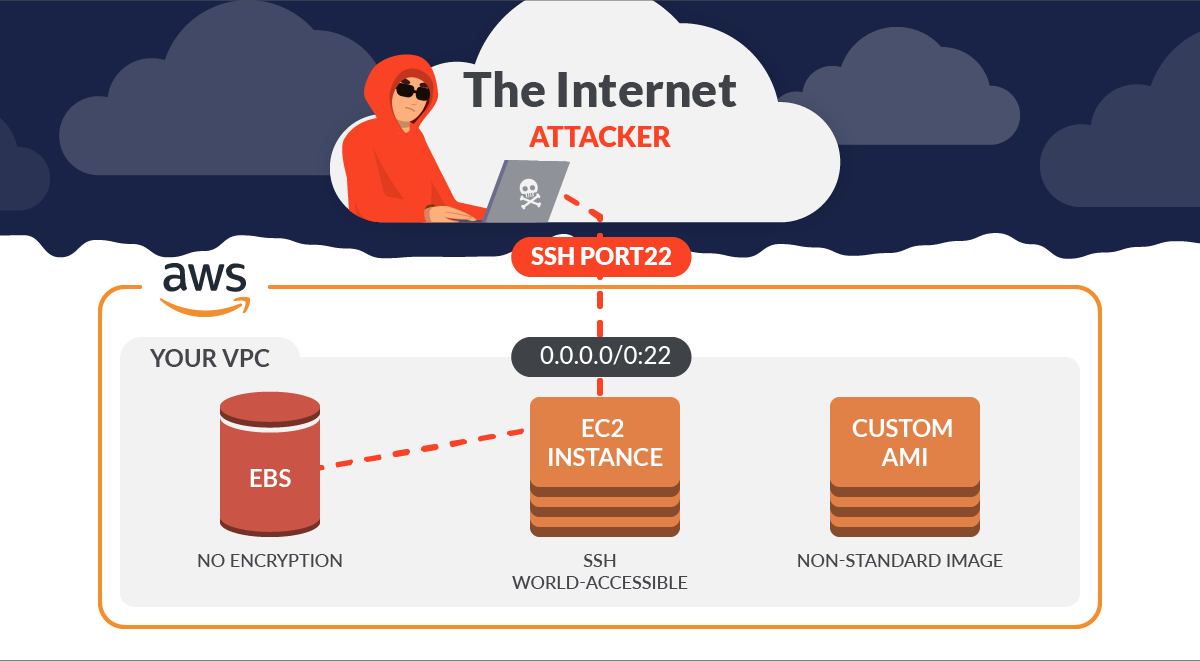
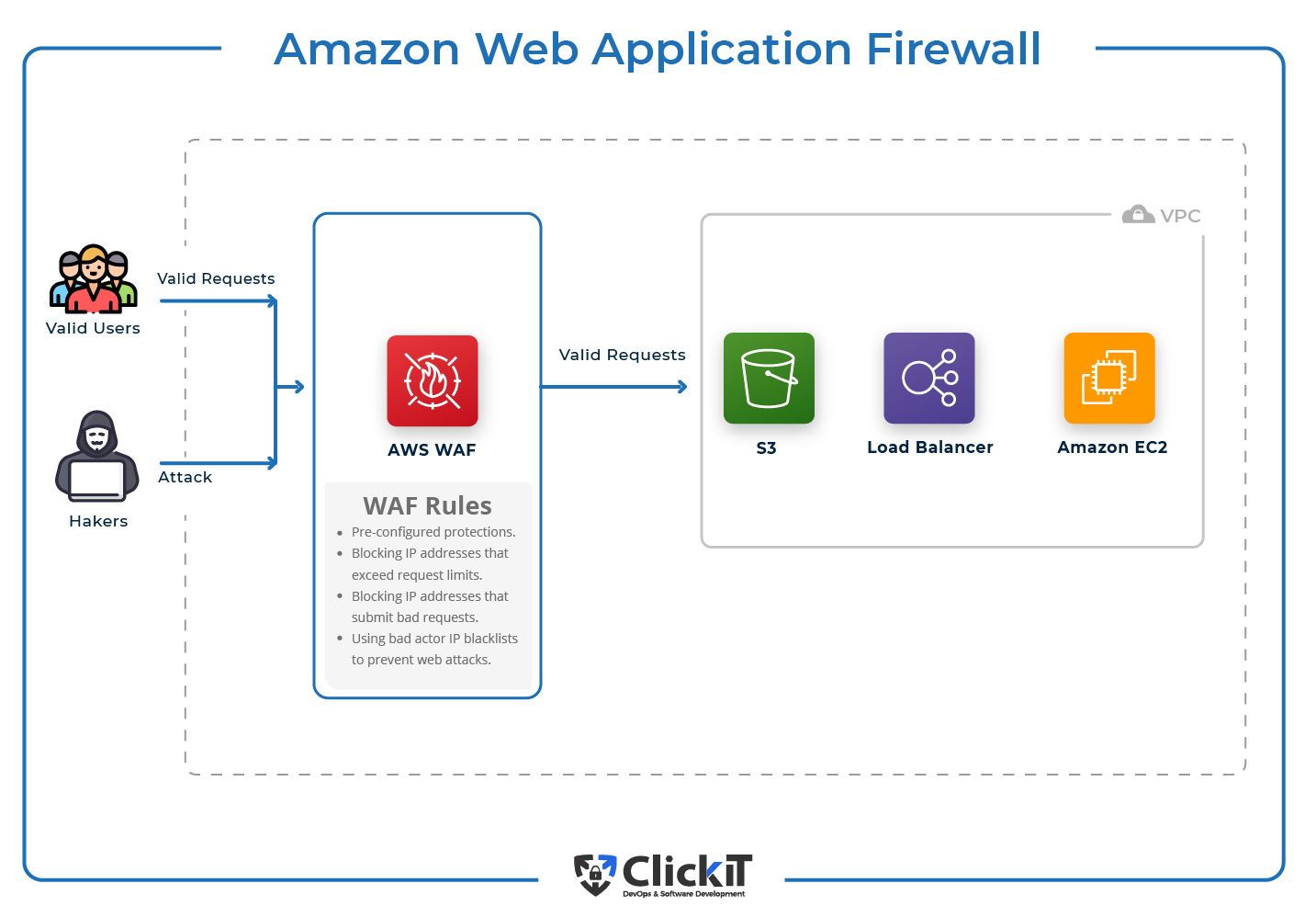



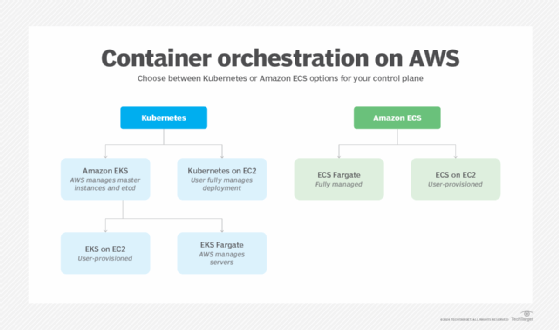

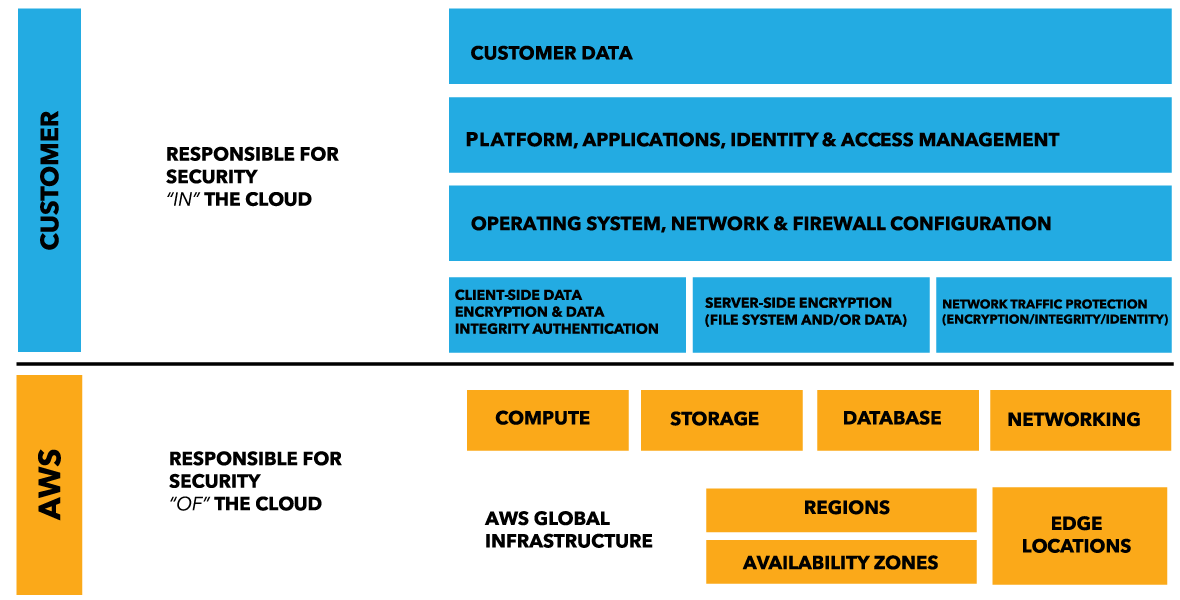


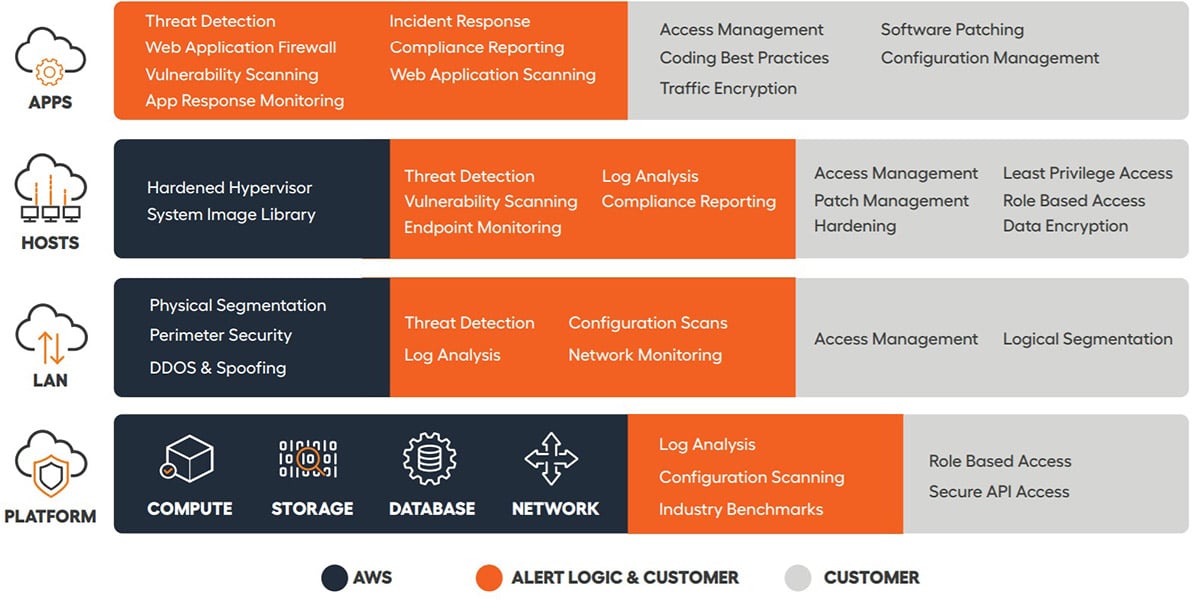











0 Response to "43 aws security best practices"
Post a Comment