44 aws best practices
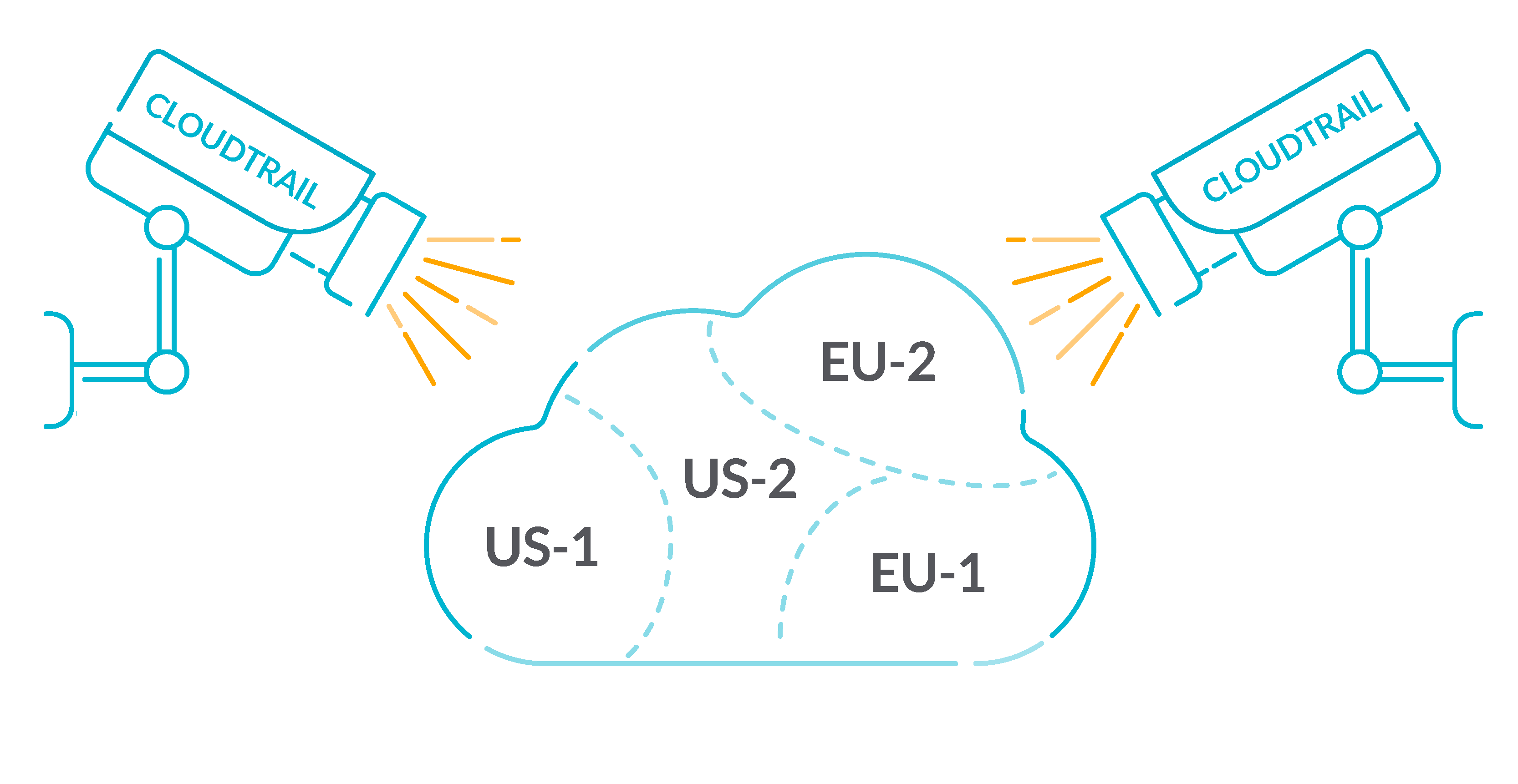
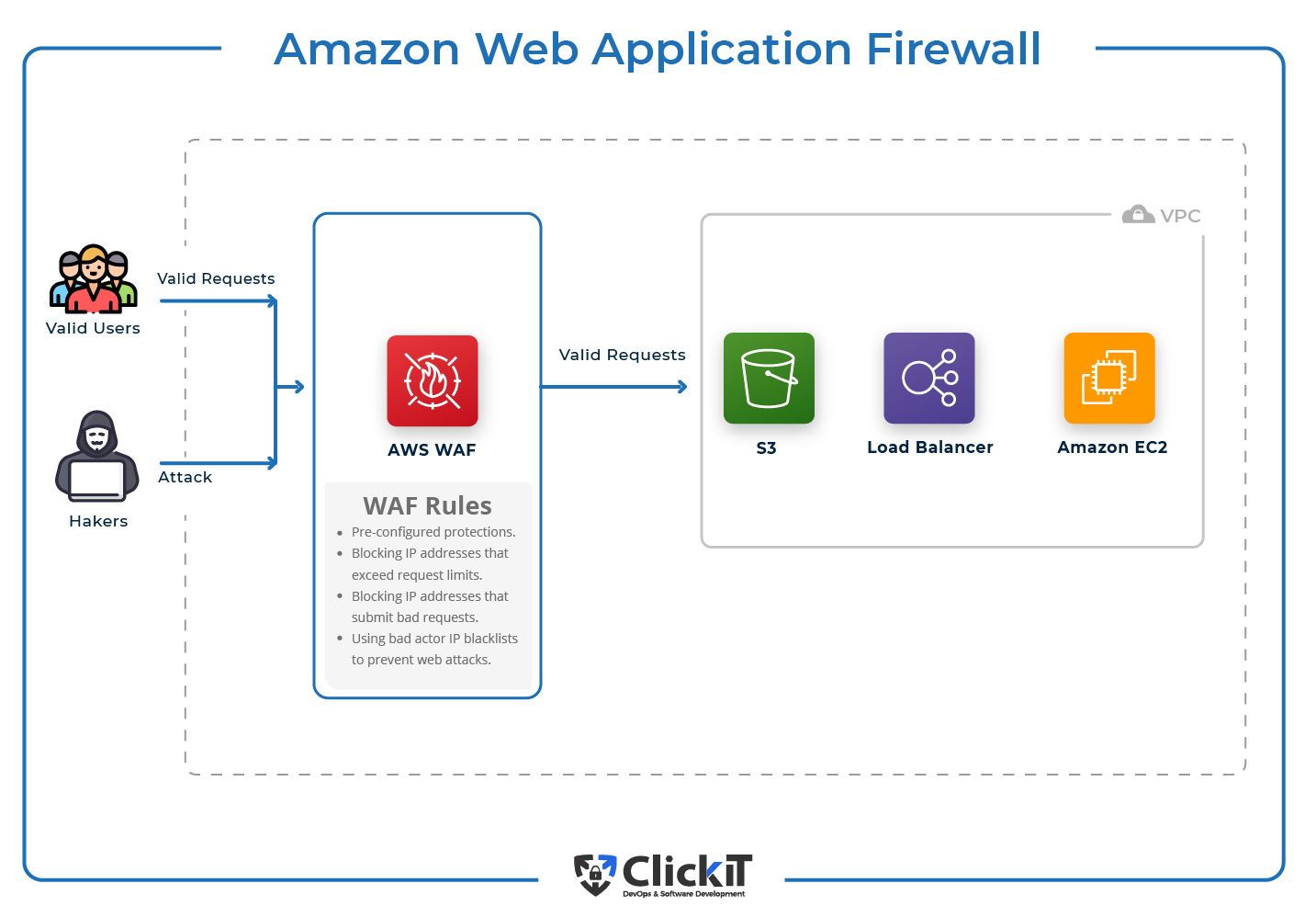
Best practices for managing AWS access keys - AWS General ... IAM Best Practices contains suggestions that help you secure your AWS resources with the AWS Identity and Access Management (IAM) service. The following topics provide guidance when you set up the AWS SDKs and the AWS CLI to use access keys: Security best practices in AWS CloudTrail - AWS CloudTrail CloudTrail detective security best practices. Create a trail. For an ongoing record of events in your AWS account, you must create a trail. Although CloudTrail provides 90 days of event history information for management events in the CloudTrail console without creating a trail, it is not a permanent record, and it does not provide information about all possible types of events.
Best practices when using Athena with AWS Glue - Amazon Athena When using Athena with the AWS Glue Data Catalog, you can use AWS Glue to create databases and tables (schema) to be queried in Athena, or you can use Athena to create schema and then use them in AWS Glue and related services. This topic provides considerations and best practices when using either method.

Aws best practices
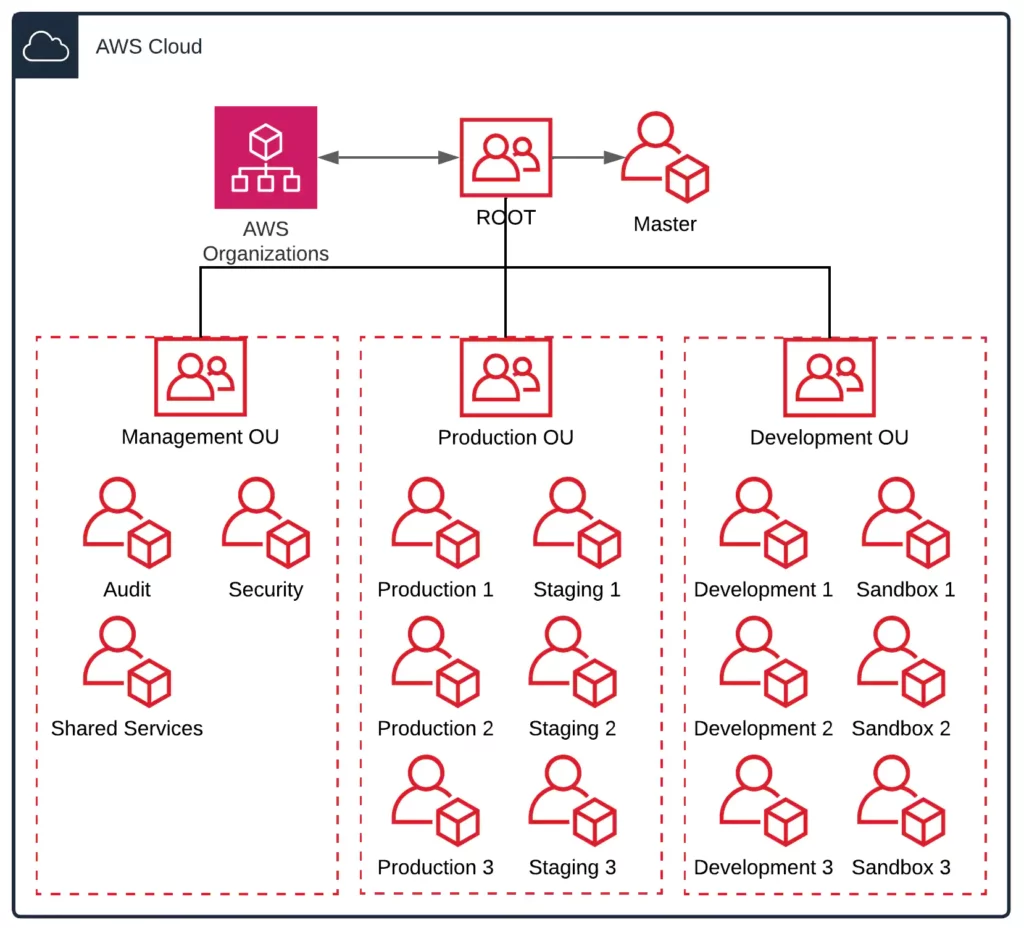
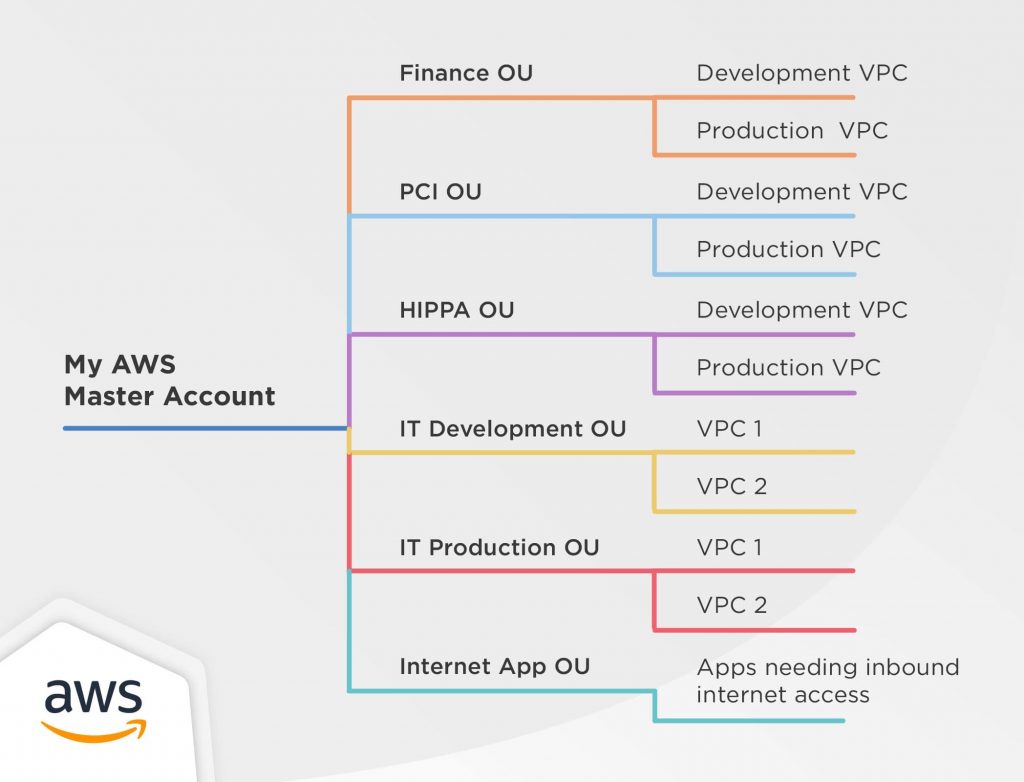
AWS Tags Best Practices and AWS Tagging Strategies Aug 12, 2020 · AWS Tags Best Practices. While there isn’t a perfect AWS tagging strategy that works for every organization, there are a few AWS tagging best practices that you should be familiar with. 1. Know how each AWS tag you create will be used. AWS cites four categories for cost allocation tags: technical, business, security, and automation. Consider ... Establishing your best practice AWS environment The rest of this guide will walk you through the elements of building a secure and productive multi-account AWS environment, often referred to as a “landing zone,” as recommended by AWS. This represents the best practices that can be used to build an initial framework while still allowing for flexibility as your AWS workloads increase over ... Security best practices in IAM - AWS Identity and Access ... Jul 14, 2022 · Use the root user to complete the tasks that only the root user can perform. For the complete list of these tasks, see Tasks that require root user credentials in the AWS General Reference. For more information, see Best practices to protect your account's root user in the AWS Account Management User Guide.
Aws best practices. Learn best practices for securing your AWS account and resources Aug 22, 2022 · For more information, see Security best practices in AWS CloudTrail. Use CloudTrail and CloudWatch in conjunction to monitor access key usage and receive alerts for unusual API calls. Activate resource-level logging (for example, at the instance or OS level) and Amazon S3 default bucket encryption . Security best practices in IAM - AWS Identity and Access ... Jul 14, 2022 · Use the root user to complete the tasks that only the root user can perform. For the complete list of these tasks, see Tasks that require root user credentials in the AWS General Reference. For more information, see Best practices to protect your account's root user in the AWS Account Management User Guide. Establishing your best practice AWS environment The rest of this guide will walk you through the elements of building a secure and productive multi-account AWS environment, often referred to as a “landing zone,” as recommended by AWS. This represents the best practices that can be used to build an initial framework while still allowing for flexibility as your AWS workloads increase over ... AWS Tags Best Practices and AWS Tagging Strategies Aug 12, 2020 · AWS Tags Best Practices. While there isn’t a perfect AWS tagging strategy that works for every organization, there are a few AWS tagging best practices that you should be familiar with. 1. Know how each AWS tag you create will be used. AWS cites four categories for cost allocation tags: technical, business, security, and automation. Consider ...


























0 Response to "44 aws best practices"
Post a Comment